We will examine Weblogic’s Active Directory integration, which provides high performance especially in database connections and a cluster structure that can be created within itself.
First of all, I should mention that our Weblogic server ran in “Production Mode” and our tests were provided between Oracle Weblogic 10.3.6 and Windows 2012 Active Directory.
First, we log in to our console via http://localhost:7001/console and open the “Security Realms” as in the marked area.
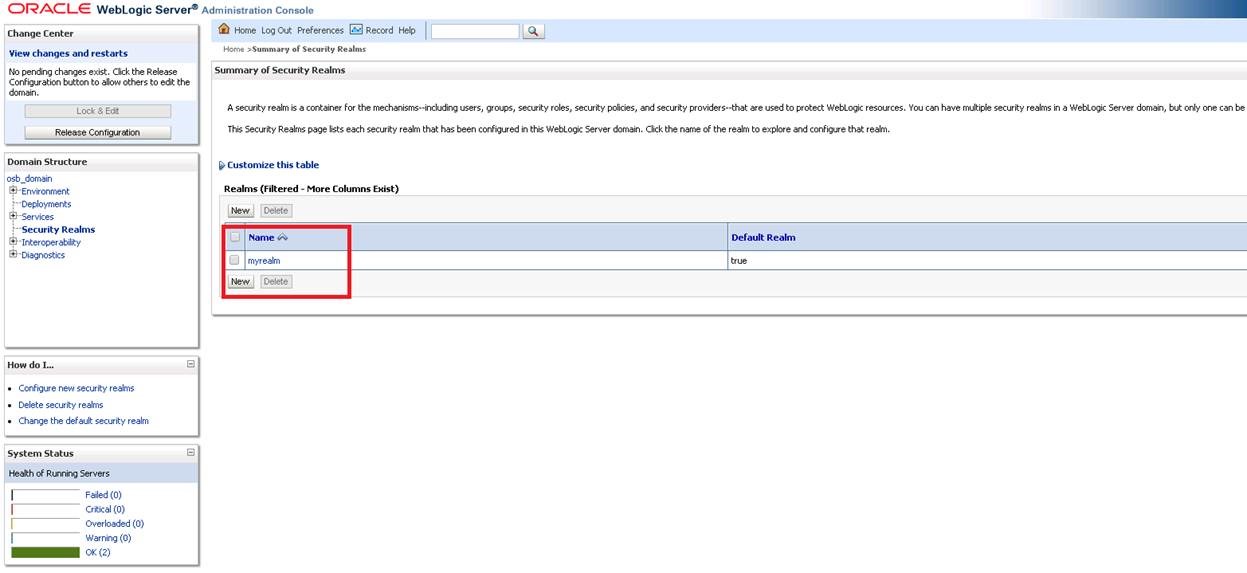
We enter “myrealm” from the screen that opens.

We make the “Security Model Default” field “Advanced” and press the “Save” button.
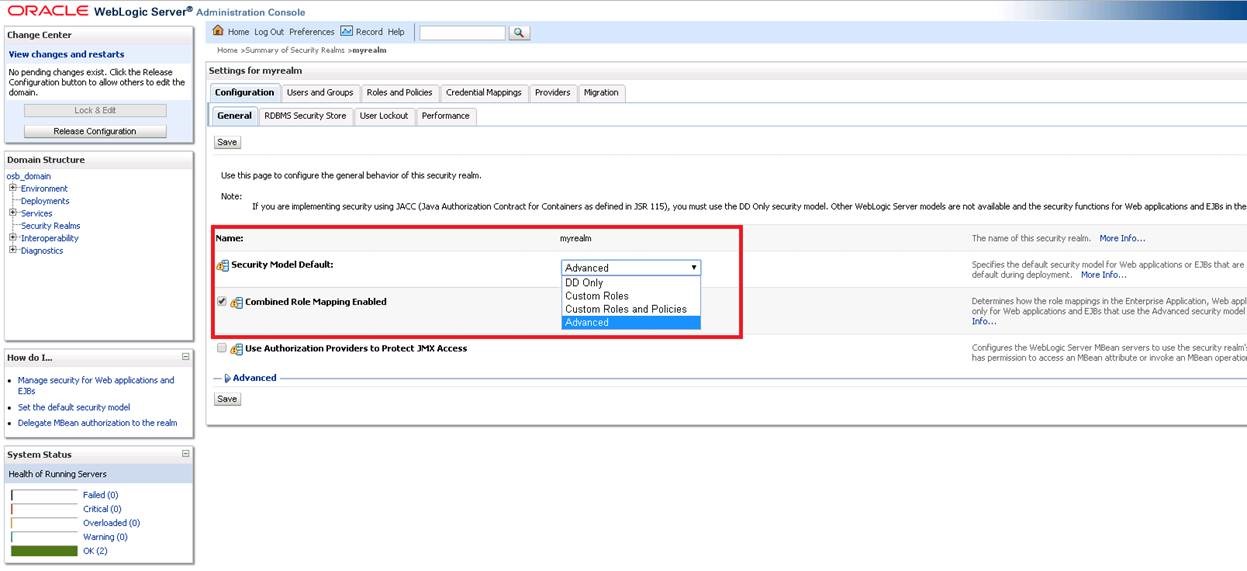
After completing the registration process, we open the ” Providers ” tab.
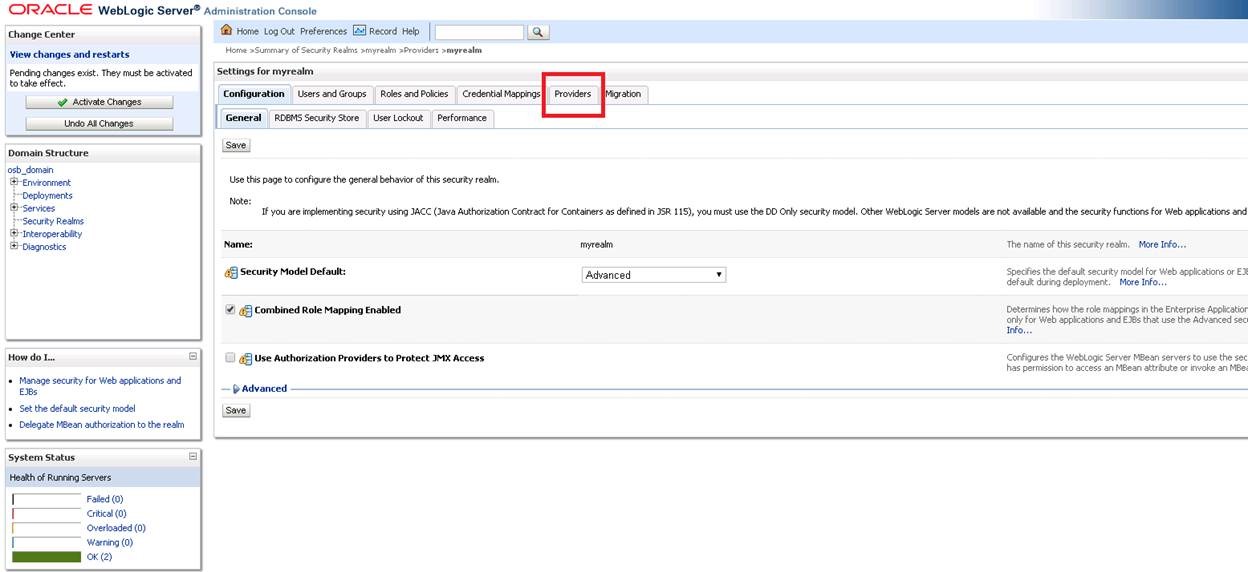
Click the “New” button on the Providers screen. We will add a new Provider for Active Directory.
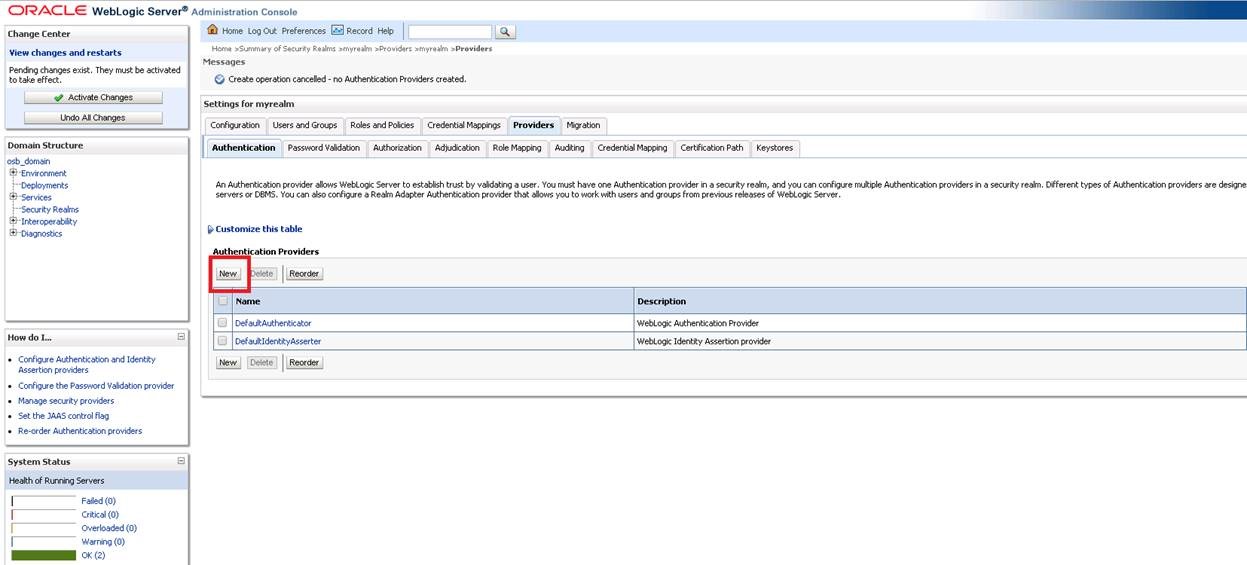
On the screen that opens, we write a name in the “Name” section and select the “Type” section as “ActiveDirectoruAuthenticator” and say “Ok”.
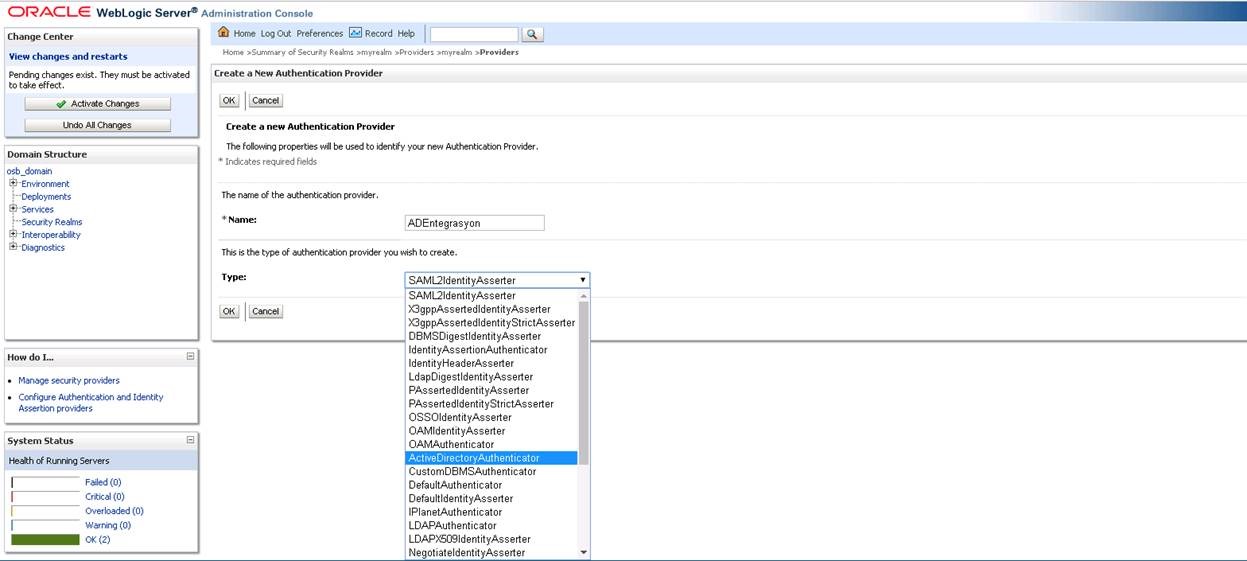
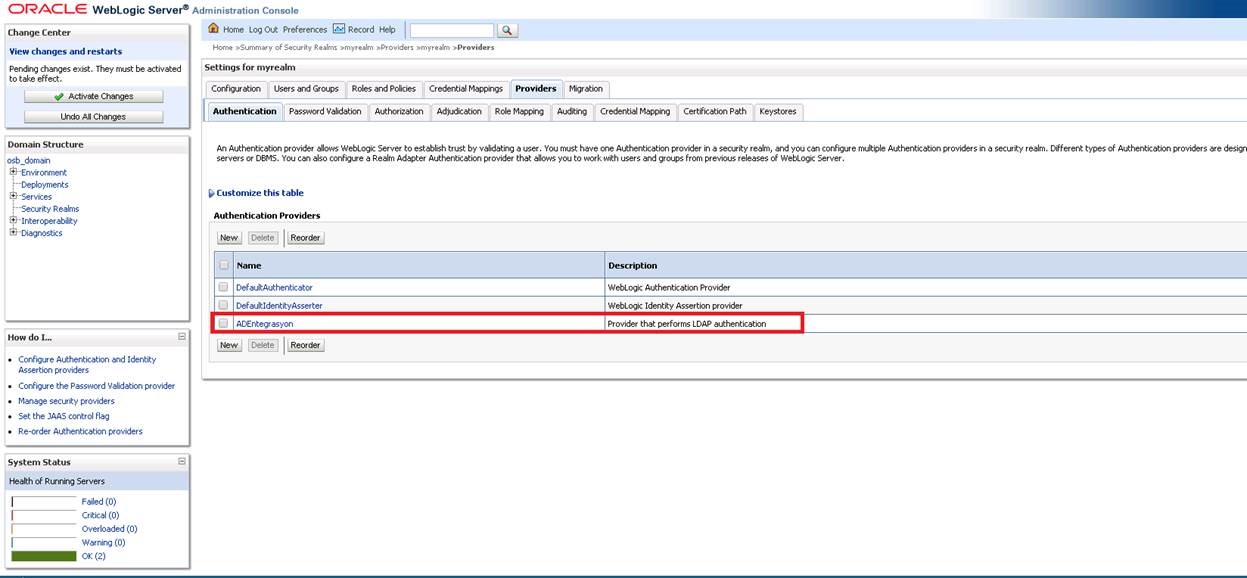
We log in to the record we added. (I added it as ADIntegration)
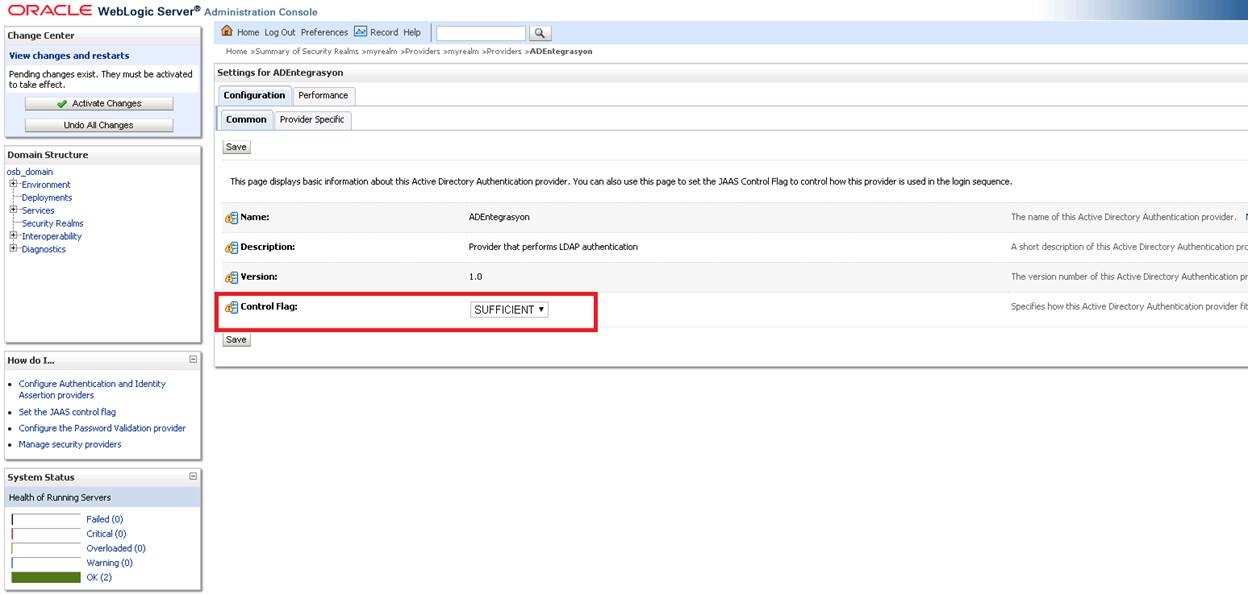
On the screen that opens, we make the “Control Flag” part “SUFFICIENT” and say “Save”.
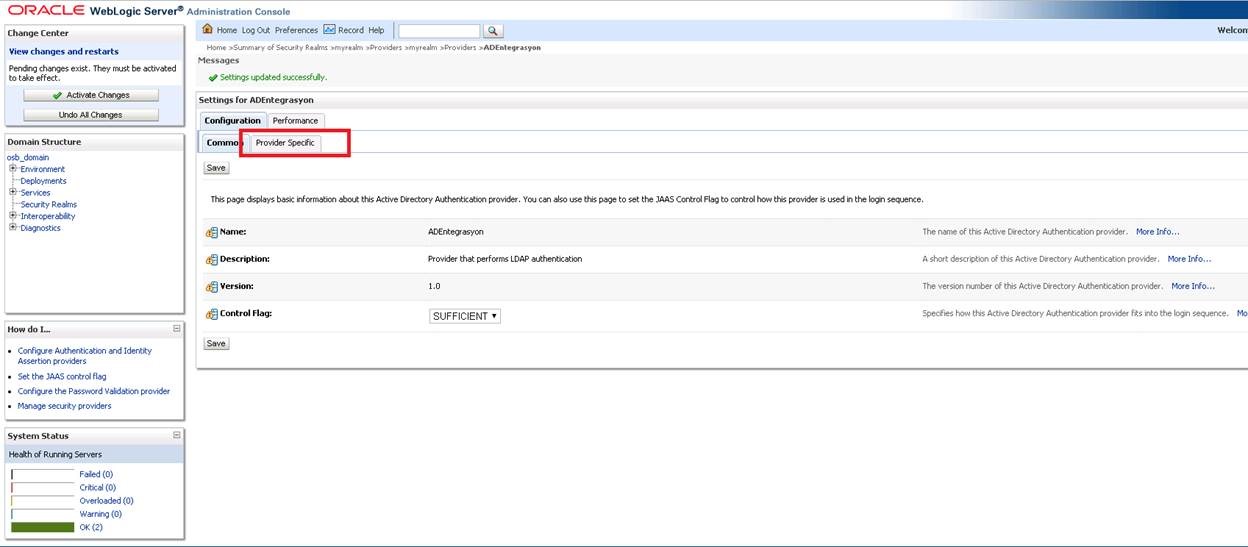
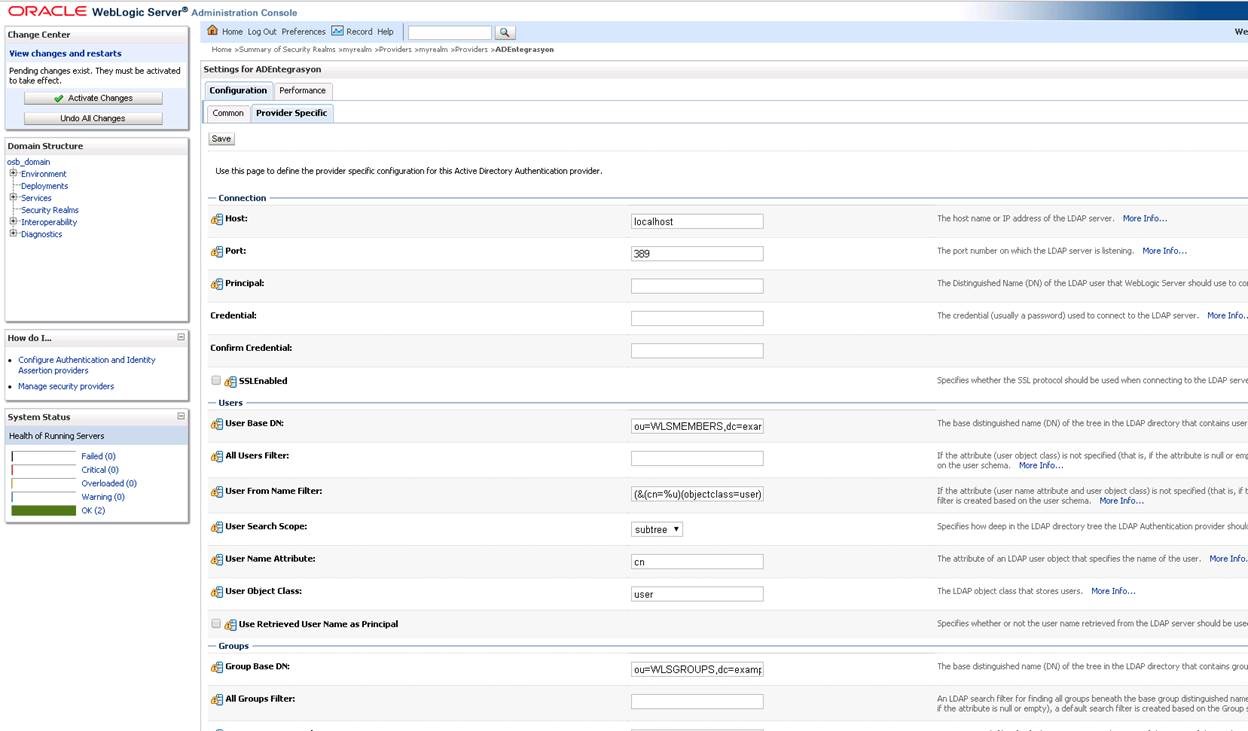
We are entering the “Provider Specific” base.
We fill the screen that opens according to our own LDAP structure. Sample template is below.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 | Host: dc.bugraparlayan.com.tr Port: 389 Principle: administrator Credential: sifre Confirm Credential: sifre User Base DN: dc=adf,dc=bugraparlayan,dc=com,dc=tr User From Name Filter: (&(cn=%u)(objectclass=user)) User Search Scope: subtree User Name Attribute: sAMAccountName User Object Class: organizationalPerson Group Base DN: ou=my-department,dc=adf, dc=bugraparlayan,dc=com,dc=tr Group From Name Filter: (&(cn=%g)(objectclass=group)) Group Search Scope: subtree Group Membership Searching: unlimited Max Group Membership Search Level: 0 Static Group Name Attribute: cn Static Group Object Class: group Static Member DN Attribute: member Static Group DNs from Member DN Filter: (&(member=%M)(objectclass=group)) |
After editing the above values according to your own structure, we press the “Save” button and complete the process by saying “Activate Changes” to save the changes.
Now we can see Active Directory users in the definitions we made.
If you are having problems with Active Directory authentication, the following points should be considered.
You must restart AdminServer and all managed servers for any Security Realm changes to take effect.
If you are going to use a user other than Administrator, you should check the permissions.
Finally, check the DNS addresses of the Weblogic server.
![]()
 Database Tutorials MSSQL, Oracle, PostgreSQL, MySQL, MariaDB, DB2, Sybase, Teradata, Big Data, NOSQL, MongoDB, Couchbase, Cassandra, Windows, Linux
Database Tutorials MSSQL, Oracle, PostgreSQL, MySQL, MariaDB, DB2, Sybase, Teradata, Big Data, NOSQL, MongoDB, Couchbase, Cassandra, Windows, Linux 