The Oracle Database Security Assessment Tool (DBSAT) analyzes database configurations and security policies to help eliminate security risks and improve database security. Using the DBSAT tool, you can implement recommended security-related actions.
With DBSAT, you can eliminate short-term security risks, and report the necessary findings to implement a comprehensive security strategy.
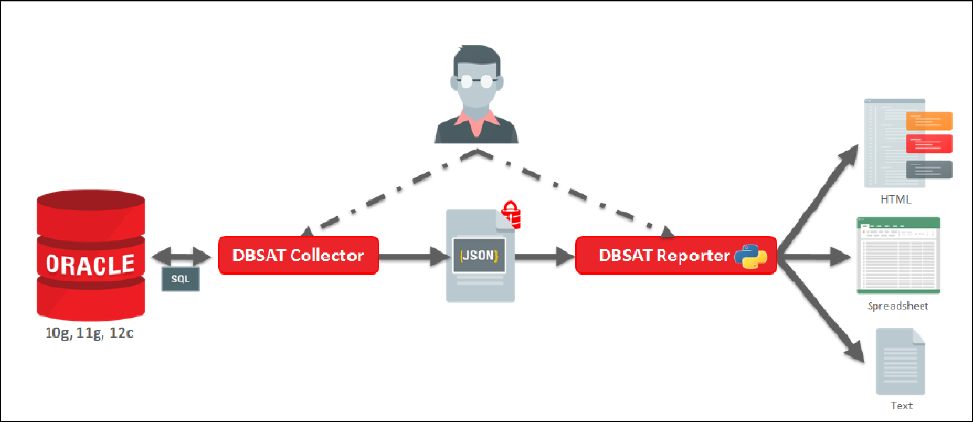
DBSAT Components
DBSAT Collector: Collects data by running sql statements and operating system commands. The collected data is written to a file for use in the analysis phase.
DBSAT Reporter: Analyzes the collected data and reports its findings in different formats. These formats can be pdf, excel and text.
The following operations can be performed using the DBSAT :
- You can quickly identify security configuration issues in your database.
- You can apply the best recommended solutions for security.
- You can improve the security of Oracle databases.
- You can reduce the attack risk.
DBSAT Usage
You can download the required files for DBSAT from the link mentioned in document 2138254.1. You can use DBSAT for Solaris x64 and Solaris SPARC, Linux x86-64, Windows x64, HP-UX IA (64-bit), IBM AIX & zSeries Based Linux platforms, and Oracle Database 10.2.0.5 and later versions.
The user to connect to the database with DBSAT must have the following privileges.
- CREATE SESSION
- SELECT on SYS.REGISTRY$HISTORY
- Role SELECT_CATALOG_ROLE
- Role DV_SECANALYST (If Database Vault is Used)
- Role AUDIT_VIEWER (Only 12c)
- Role CAPTURE_ADMIN (Only 12c)
- SELECT on SYS.DBA_USERS_WITH_DEFPWD (11g and 12c)
- SELECT on AUDSYS.AUD$UNIFIED (Only 12c)
Python 2.6 or higher is required for reporting. You can find the Python version in the system with the following command.
1 2 | [root@exadb01 ~]# python -V Python 2.6.6 |
You must extract the dbsat.zip file downloaded from the link in the document, in the Oracle home directory. You can use the dbsat tool by setting environment variables. ORACLE_HOME and ORACLE_SID
1 2 3 | [oracle@exadb01 ~]$ . oraenv ORACLE_SID = [EXADB1] ? The Oracle base remains unchanged with value /u01/app/oracle |
The DBSAT Collector can be run as follows.
1 | dbsat collect <connect_string> <destination> |
The full file path should be specified with the destination and a name must be given to the database.
Example: for exadb database,
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 | [oracle@exab01 dbsat]$ ./dbsat collect system/welcome1 /home/oracle/dbsat/exadb Database Security Assessment Tool version 2.0.1 (December 2017) This tool is intended to assist in you in securing your Oracle database system. You are solely responsible for your system and the effect and results of the execution of this tool (including, without limitation, any damage or data loss). Further, the output generated by this tool may include potentially sensitive system configuration data and information that could be used by a skilled attacker to penetrate your system. You are solely responsible for ensuring that the output of this tool, including any generated reports, is handled in accordance with your company's policies. Connecting to the target Oracle database... SQL*Plus: Release 11.2.0.4.0 Production on Mon Apr 2 12:12:48 2018 Copyright (c) 1982, 2013, Oracle. All rights reserved. Connected to: Oracle Database 11g Enterprise Edition Release 11.2.0.4.0 - 64bit Production With the Partitioning, Real Application Clusters, Automatic Storage Management, Oracle Label Security, OLAP, Data Mining and Real Application Testing options Setup complete. SQL queries complete. /bin/cat: /u01/app/oracle/product/11.2.0.4/dbhome_1/network/admin/sqlnet.ora: No such file or directory Warning: Exit status 256 from OS rule: sqlnet.ora /bin/ls: cannot access /u01/app/oracle/product/11.2.0.4/dbhome_1/network/admin/sqlnet.ora: No such file or directory Warning: Exit status 512 from OS rule: ls_sqlnet.ora /bin/cat: /u01/app/oracle/product/11.2.0.4/dbhome_1/network/admin/listener.ora: No such file or directory Warning: Exit status 256 from OS rule: listener.ora /bin/ls: cannot access /u01/app/oracle/product/11.2.0.4/dbhome_1/network/admin/listener.ora: No such file or directory Warning: Exit status 512 from OS rule: ls_listener.ora OS commands complete. Disconnected from Oracle Database 11g Enterprise Edition Release 11.2.0.4.0 - 64bit Production With the Partitioning, Real Application Clusters, Automatic Storage Management, Oracle Label Security, OLAP, Data Mining and Real Application Testing options DBSAT Collector completed successfully. Calling /u01/app/oracle/product/11.2.0.4/dbhome_1/bin/zip to encrypt exadb.json... Enter password: Verify password: adding: exadb.json (deflated 86%) zip completed successfully. |
When you run the command, it will ask for the password to be specified for the zip file. After the command runs, a file (exadb.zip) will be created in the specified directory (/ home / oracle / dbsat) with the specified name. This file contains the data to be used for reporting.
DBSAT Reporter can be run as follows.
1 | dbsat report [-a] [-n] [-x <section>] <pathname> |
With -a, it includes all users in the database during analysis. Unless specified by -a, it does not include users who cannot access the database, such as expired or locked users.
With -n, it is ensured that the report is not encrypted.
With -x, it ensures that some sections are not included in the report. These sections are as follows:
– USER : User Accounts
– PRIV : Privileges and Roles
– AUTH : Authorization Control
– CRYPT : Encryption
– ACCESS :Fine-Grained Access Control
– AUDIT : Auditing
– CONF : Database Configuration
– NET : Network Configuration
– OS : Operating System
Sample Usage: :
1 | -x USER,PRIV yada —x USER —x PRIV |
Example: for exadb ,
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 | [oracle@exadb01 dbsat]$ ./dbsat report -a exadb Database Security Assessment Tool version 2.0.1 (December 2017) This tool is intended to assist in you in securing your Oracle database system. You are solely responsible for your system and the effect and results of the execution of this tool (including, without limitation, any damage or data loss). Further, the output generated by this tool may include potentially sensitive system configuration data and information that could be used by a skilled attacker to penetrate your system. You are solely responsible for ensuring that the output of this tool, including any generated reports, is handled in accordance with your company's policies. Archive: exadb.zip [exadb.zip] exadb.json password: inflating: exadb.json DBSAT Reporter ran successfully. Calling /usr/bin/zip to encrypt the generated reports... Enter password: Verify password: zip warning: exadb_report.zip not found or empty adding: exadb_report.txt (deflated 85%) adding: exadb_report.html (deflated 87%) adding: exadb_report.xlsx (deflated 3%) adding: exadb_report.json (deflated 88%) zip completed successfully. |
When the command is executed, a file named “<pathname> _report.zip” (exadb_report.zip) will be created in the same directory. The password for this compressed file is the password that is issued when the command is executed. There are reports in html, excel and text format in the file.
![]()
 Database Tutorials MSSQL, Oracle, PostgreSQL, MySQL, MariaDB, DB2, Sybase, Teradata, Big Data, NOSQL, MongoDB, Couchbase, Cassandra, Windows, Linux
Database Tutorials MSSQL, Oracle, PostgreSQL, MySQL, MariaDB, DB2, Sybase, Teradata, Big Data, NOSQL, MongoDB, Couchbase, Cassandra, Windows, Linux 