Most DBA usually define the SQL Server Service Account as the Administrator on the server.
Actually, this authority is not necessary. You must not give any user more authority than required for information security.
The minimum privileges that a SQL Server Service Account can run are as follows;
Log on as a service(SeServiceLogonRight)
Replace a process-level token (SeAssignPrimaryTokenPrivilege)
Bypass traverse checking (SeChangeNotifyPrivilege)
Adjust memory quotas for a process (SeIncreaseQuotaPrivilege)
To define these authorities, we write secpol.msc in windows home on the SQL Server server and press ENTER.
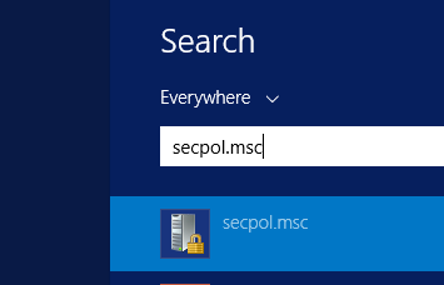
In the screen that appears, we select Local Policies and User Rights Assignment.
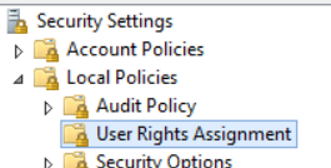
In the incoming screen, double click on the policies indicated in the previous 4 items one by one and click on Add User or Group where you see the screen below to add the sql server service account and click OK.
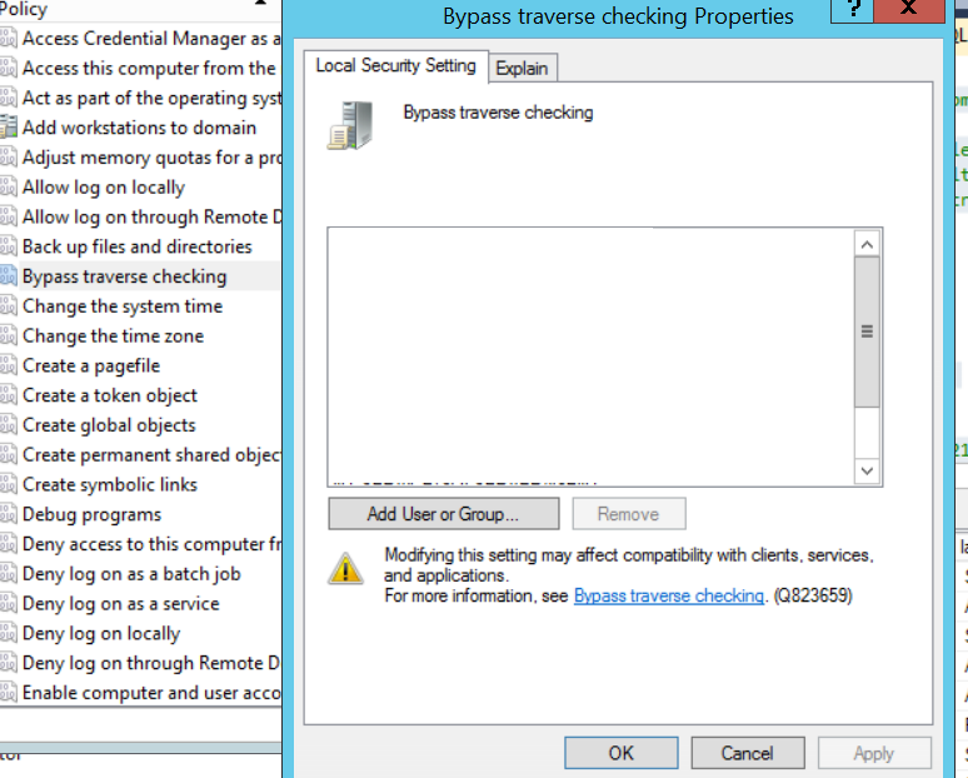
You should do the same for the 4 policies I mentioned.
You should also set lock pages in memory and perform volume maintenance task for performance.
You can get detailed information about last two policy in the below articles.
“Numa Nodes, MAX / MIN Server Memory, Log Pages In Memory and MAXDOP“,
“Instant File Initialization(Restore or Allocate Disk Space Faster)”
![]()
 Database Tutorials MSSQL, Oracle, PostgreSQL, MySQL, MariaDB, DB2, Sybase, Teradata, Big Data, NOSQL, MongoDB, Couchbase, Cassandra, Windows, Linux
Database Tutorials MSSQL, Oracle, PostgreSQL, MySQL, MariaDB, DB2, Sybase, Teradata, Big Data, NOSQL, MongoDB, Couchbase, Cassandra, Windows, Linux 