In this article, we will install winlogbeat in Windows Server 2019(10.250.2.224) in order to monitor windows event logs, make necessary configurations to transfer event logs to logstash, and run winlogbeat as a service.
Let’s download the winlogbeat from https://www.elastic.co/downloads/beats/winlogbeat on our server and unzip it to the C drive.
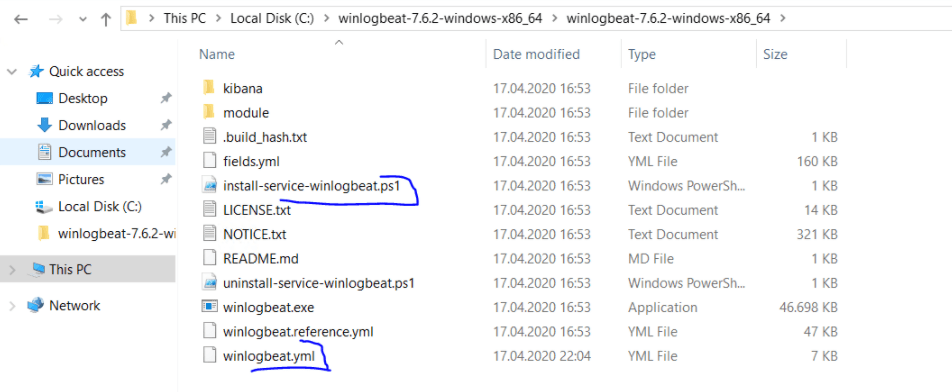
Let’s make a few notes about the files in the Winlogbeat folder.
What is winlogbeat.yml File?
The winlogbeat.yml file is the basic config file and we enter information about which windows events it should monitor and how long it should monitor these logs. In addition, we enter the logstash information that will transfer these logs, into this file.
What is winlogbeat.reference.yml File?
The winlogbeat.reference.yml file provides us with a full configuration example.
What is install-service-winlogbeat.ps1 File?
Thanks to the install-service-winlogbeat.ps1 power shell script file, we run the winlogbeat as a service.
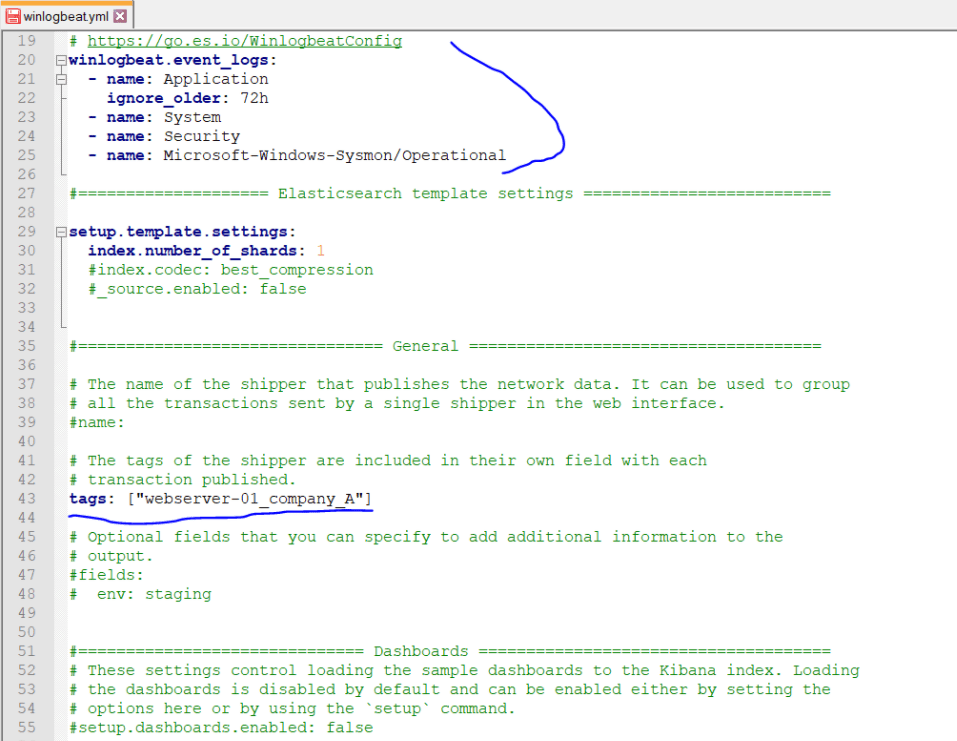
Configure winlogbeat.yml
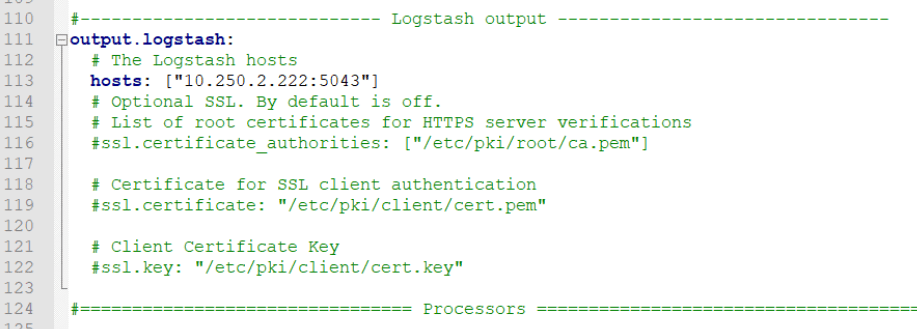
Now let’s do the configurations in winlogbeat.yml config file. According to this configuration; We specify that we want to monitor Application, System, Security and Microsoft-Windows-Sysmon logs in windows eventlogs. And we state that we will ignore Application logs before 72 hours, and we state that we want to send these logs to port 5043 of logstash running at 10.250.2.222.
Start winlogbeat Service
Now, when we run the install-service-winlogbeat.ps1 power shell script, the winlogbeat will be ready to run as a service. As soon as we run the winlogbeat service, it will start sending logs to logstash.
1 2 | PS C:\winlogbeat-7.6.2-windows-x86_64\winlogbeat-7.6.2-windows-x86_64> .\install-service-winlogbeat.ps1 PS C:\winlogbeat-7.6.2-windows-x86_64\winlogbeat-7.6.2-windows-x86_64> Start-Service winlogbeat |
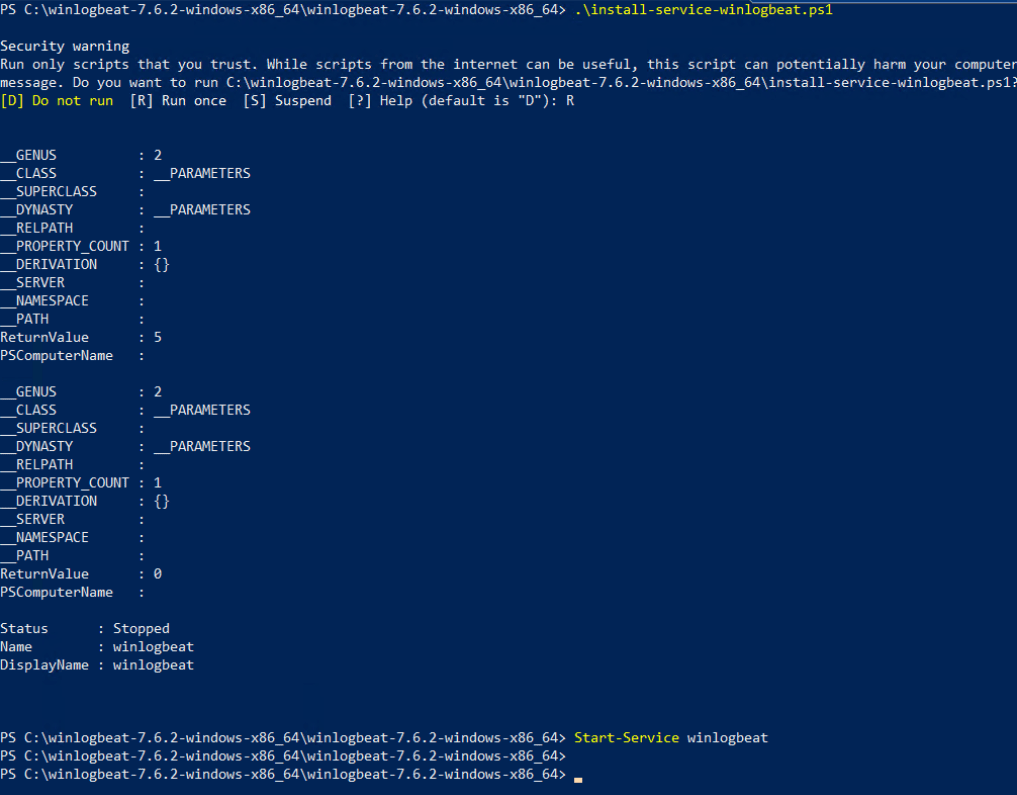
Now Winlogbeat has started to work as a service, we can confirm this from the task manager. However, since we do not configure logstash at the moment, it keeps event logs on itself. When we complete the logstash configuration, logs will be successfully transferred to logstash. In my next article I will be configuring the logstash.
You can read our other articles in this serie from the links below.
Install Elasticsearch on ubuntu server 19.10
Install Logstash on Ubuntu Server 19.10
Install Kibana on Ubuntu Server 19.10
Install Winlogbeat on Windows Server 2019
Configure Logstash to Read log files Windows
Create Kibana Dashboards For Windows Event Logs
![]()
 Database Tutorials MSSQL, Oracle, PostgreSQL, MySQL, MariaDB, DB2, Sybase, Teradata, Big Data, NOSQL, MongoDB, Couchbase, Cassandra, Windows, Linux
Database Tutorials MSSQL, Oracle, PostgreSQL, MySQL, MariaDB, DB2, Sybase, Teradata, Big Data, NOSQL, MongoDB, Couchbase, Cassandra, Windows, Linux 